Extracting the private key into a PEM file from a PKCS12 file transmitted over UDP allows the investigator to decrypt an RDP session and recover some secret data.
Challenge Description
Points
666
Description
One of our boxes was pwned. During the post-mortem, we found something
called mimikatz which we didn't install so we wiped and reinstalled the
box. However, we forgot to backup our flag file. Luckily, we have a
network capture of the attacker exfiltrating the file. CAN YOU PLEASE
RECOVER OUR FLAG FILE?
Files
Solution
There are two distinct streams in the PCAP file: a UDP stream and a large TCP stream.
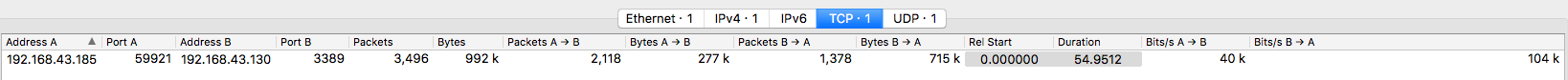
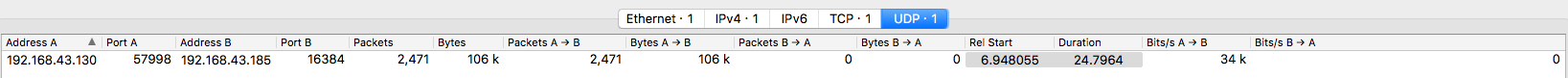
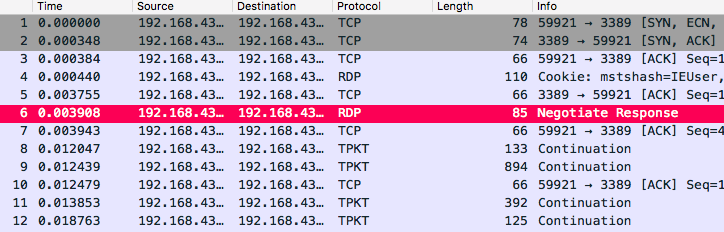
We can see that the TCP stream holds RDP data when we analyse the start of the traffic. If it does not show up like that for you when you open the PCAP file, decode the TCP traffic as TPKT.
Also, we note that the RDP traffic is encrypted over SSL as negotiated here:
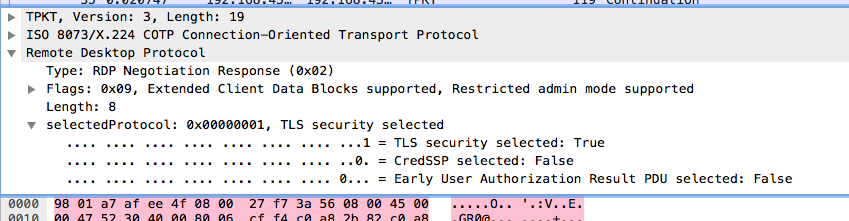
From this, we can guess that we need to replay the RDP session but to do that we need to find a key to decrypt the communication. This would probably be in the UDP stream.
Following the UDP stream, we see a ton of binary data with some interesting strings in them. “TSSecKeySet1” and “Microsoft Strong Cryptographic Provider” look like very interesting references to the crypto stuff we want to find.
We can dump the entire stream to a file and try to analyse it. First, let’s see if it’s recognisable as a file:
$ file extracted_data.bin
extracted_data.bin: data
It looks like it does not have a recognisable header. So let’s try running binwalk on it:
$ binwalk -e extracted_data.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
30 0x1E Certificate in DER format (x509 v3), header length: 4, sequence length: 2376
57 0x39 Certificate in DER format (x509 v3), header length: 4, sequence length: 1466
1546 0x60A Private key in DER format (PKCS header length: 4, sequence length: 860
Now it seems like it contains some certificates and a private key in it. Trying to convert the individual files to something plaintext we can read with openssl did not seem to work. We can debug this by reading it as ASN.1.
$ openssl asn1parse -inform DER -in extracted_data.bin
0:d=0 hl=4 l=2467 cons: SEQUENCE
4:d=1 hl=2 l= 1 prim: INTEGER :03
7:d=1 hl=4 l=2399 cons: SEQUENCE
11:d=2 hl=2 l= 9 prim: OBJECT :pkcs7-data
22:d=2 hl=4 l=2384 cons: cont [ 0 ]
26:d=3 hl=4 l=2380 prim: OCTET STRING [HEX DUMP]:30820948308205D106092A864886F70D010701A08205C2048205BE308205BA308205B6060B2A864886F70D010C0A0102A08204F6308204F2301C060A2A864886F70D010C0103300E040866AFD4385D4302C4020207D0048204D093F23B4782B6438E5CB094A8C35CF1352F486FA1F7E3708A3F1BFC865A5EEF3C931DC82BA36EEF23609FE4717D0A021EEF8A981021BDADD04AFA64131A546CE65191A88C001ADCA9A5A15EDB1178E0DADDDCEDDCC3AB13BAADAE35B2B87378CC9158C0145DB1EB300E129D265C92E2C726E4790DA9F34AD0B80AF7BFD152B7AF4DD97B9B3BC4057CA245E4B871B871023F96832DCA3A4BA3E8628C34ACB48C75497CB8949CA48D1EF939495F2A0BE4B7497E0C19659EBE083ABFD8268D97149418C969CE28112F31255383994AA95B50C7A15285477A6D01B955E80C9F961FD03226C8233CA6F4851318D0B22B5B0E4D536CDF729827F2A12289E789675DDE3BBDC339376447AF09CD807AF811D216D148126B42177D7F1634BFAB0BB959A485BE82F7CE08FA8468FE526D48B02CA70CAF5EA55B786E7659DAFEFFC8292E15C251BC48D27F15860BD32E2FB67FB70DDED2CB7D199ECF107FEB5F57CA6D7D83ACA47DD20D23E3F7F73AF93753F1D6E6C42060A2F0A19CA9905CFCA4705F8DA96287D57584E9D0C9FEE127A1F8E91E6AA112FDD0AA42714BBFBDF1DB07BED4D3BB70B2AE3D614F75E17B8932E3ADCB8077DBE6EB9A3B723DFE7000B0B8DAD199D8FF4B8501BE45671BCAA8F3F5A9EB9EE67805F91C0734BE00F7EFDEAD031308879A852612AE3910830086EF4BC3CD6F9C14C5FA50F563EAB57C89F6AA49BBDF923D5E8847017C2F134AC4777E4E52D1DDDC1CCDDF800CC07DE1E733C8D233508E88306A0C9A035B1B61FA386F10CB1841C05C3442CAC764B0A5276A1047BF6EFA0E621A2FAE1A8792D8C5E20F692A472D88F96B32EB3D18B066BBEC04DAC120ADD3A0AFDAA2D81DF0A2CAFD1C135A0EC7AAEF4474B2853C125487DE8A7623F25F0029F912F9F689DD0AD5F4275FC8DFB6ADD908B677D3975AFBC207B0B24D225EDF28F88C17C451D6F0A8521CA55B873F611C742C5C7525B04C6C3E2BA0BC59D43C02EE517BA8D08E102F9837A6B37C505D2BD97D23AB4F6912B5EB67747EB572969057B923D347980E7F3338F2E70AE1E13B2071D9DD84991937B676838F8C42BB6A36A06A78B895063CBF9E20FD445EC96CF886D58FCA47230593FE7DA25535BBDAD2BED116FCF0A47BFEE90F6C0C227A5B9DFA33BDAB645585EBD3CC402DE595FF1A016A1B73472580FB2CB271CCEDFF473916D72334E4D5F4674EBA649636B00D05C852FFDF930360DCEFF949BEA357AF1DE79DD503E9705BAE51488F3B5F4468F15FC17593B7C06E2E5D7A26D02112E28034ED3D5C2956159CD2440D8B03BBA8E227608FE9C12FF0C0A12600AE3A3938AF7DDAB4BED9243A891D4EE684F5A0EC60DA908C5167F0302BBFB8940817D4C7D2F242DB6A980F196A2FF973223D73866B4E226D3F6EEB8177536FB10DA9E7BD864B0020C636F3A3673761A17B6865992FB0755AE9EB8036AA41776294D0FF8EA6F12CC9ECB45D45B154F2BF03B0A70E2B42DA1A7F99AA3FD4819857118FD77666D476C3C9BD258377994FB49EB5E820B416CCC5449895DEF2EAE3637CC8D5828D9DA7F1727FAEB740A7148BE35A4A689C75D152DD4DD431EAEA135E3AC5384BF7A226971B5BE18E041D046843F9BE8552292DF886C97F010DE239C4DD431163A88AB440BF14BD8B69D409C48366F289E59282EDE9796CAD4A1975FF52A2332DAC6756CB25AA24273B90E22B2B133A5C3F0805160E510B192D6BC18370F43181AC300D06092B06010401823711023100301306092A864886F70D0109153106040401000000302706092A864886F70D010914311A1E1800540053005300650063004B006500790053006500740031305D06092B060104018237110131501E4E004D006900630072006F0073006F006600740020005300740072006F006E0067002000430072007900700074006F0067007200610070006800690063002000500072006F007600690064006500723082036F06092A864886F70D010706A08203603082035C0201003082035506092A864886F70D010701301C060A2A864886F70D010C0106300E0408135DB999CA2CD6B1020207D0808203287D8BDD108BE4C5084D46D3A88CED4C6412DF2FA7D5346D9FB289B1DC4AF4AD2B791EDA0612555A56EC21EECD6FDCCF6E83647E8DDED72942F24F551FFCFB55B7181AE5D9B6B790EA8B3B27820139681726348100035B7D349B3F77FB5265FA83B73008FC1A4687687F30A3BFF0D7289BFBC82423D753F380B53B607E7C8A101B53781D0F0273F7C1E4E42E71E2739659A569A465710B3E34C1C9165592F5DD145ECCCE570C3F3E84606D5A14878DA6172F6DB403C3FC7AF92512B8406693D4405BD27070F58A8778C3AA8D71BDDD24327F4FC2BFD932E431B99CDD461B21B57B5D8F88E90597FDD2BCB709AF6CAA264E58C116D018DE4DEA7870B7C3BCC64A8E2A1EE29EA8CCA17A7D29B2C033E2F50ACE0E01A87E7CF24CBCB8A9F7366C95F05ACFB233670952CA38B265CC3FC0F6D5575B7B02C50E9C0E54FDE359D0D216A80F3C817166DE479B94D81EE0FC1130392E5BBABCD6E11D807A7FEE2F958C3785A5857BBBFCD1B1EC8DA4D3ABFD6E3077CEB5B572C5549660B73CD3981819B2ECE1527316E5DC3DC8A0A9BFADD6A0C0065E9A8E7E1F1C2F09166629DEDC0AC57B9328C112CF77B4F3CF0118102B94BD80B01B845B03BF079B2C4F9E461958F36FFDB7886C025A3A37D4D8E9E1804C773122FF6409FE819C4A50C1267058E93F6698DBD5D2D4D7D2EB6B4443C8D1AD0E253C1D7DFE23E3918D1F6399EBD4CB4FC9EFE18D83DF575C06F5D21F824297E26999A4DA9FBCFB626CDDF0B2A9FDAB56CAF10785FAAD847D8589AFF8B0A39601CB1BF6B6256E4FB65BABAFFC5C4E5208121E4175071D18763F9152962AE964DB271313D77B488C9A1AC176ADCE6E3B3A1DC092CA5A304B3FE93C1F8F4A58D8E1992C3445180FFD1EC126690E12FF09FCED1306B4D5BEB150888E15B435AEB3316FFA019C7B89AFE0D6823C459252AF9B30E643FAC481ABE6C5E6B09C1F0B7AEEFC6FA2FC40E6BF6741273C4CFEF2529B645DFE5B7FF18AF6B9FD6443B9D206BA2F1264A073DD1DF80E554D64DBFC934657C63BF5441CE223C1AF271C73525177ABCA5D8777916BF6D22908F3C22989349E3346BE0A4712FCF0A215B4A1F06C700A88290DA38FF6BF7B9C58DC01F0E35702F49F70C6858E2D75
2410:d=1 hl=2 l= 59 cons: SEQUENCE
2412:d=2 hl=2 l= 31 cons: SEQUENCE
2414:d=3 hl=2 l= 7 cons: SEQUENCE
2416:d=4 hl=2 l= 5 prim: OBJECT :sha1
2423:d=3 hl=2 l= 20 prim: OCTET STRING [HEX DUMP]:C6636BA1DC7A4063D2AD49F7DBB800AD92260253
2445:d=2 hl=2 l= 20 prim: OCTET STRING [HEX DUMP]:9BADF56CE6069E1EB9339E0E9FCD096ACD0DBC5B
2467:d=2 hl=2 l= 2 prim: INTEGER :07D0
We get a whole ton of data. However, since the structure can contain nested data, we can drill down by specifying the octet string to decode.
$ openssl asn1parse -inform DER -in extracted_data.bin -strparse 26
0:d=0 hl=4 l=2376 cons: SEQUENCE
4:d=1 hl=4 l=1489 cons: SEQUENCE
8:d=2 hl=2 l= 9 prim: OBJECT :pkcs7-data
19:d=2 hl=4 l=1474 cons: cont [ 0 ]
23:d=3 hl=4 l=1470 prim: OCTET STRING [HEX DUMP]:308205BA308205B6060B2A864886F70D010C0A0102A08204F6308204F2301C060A2A864886F70D010C0103300E040866AFD4385D4302C4020207D0048204D093F23B4782B6438E5CB094A8C35CF1352F486FA1F7E3708A3F1BFC865A5EEF3C931DC82BA36EEF23609FE4717D0A021EEF8A981021BDADD04AFA64131A546CE65191A88C001ADCA9A5A15EDB1178E0DADDDCEDDCC3AB13BAADAE35B2B87378CC9158C0145DB1EB300E129D265C92E2C726E4790DA9F34AD0B80AF7BFD152B7AF4DD97B9B3BC4057CA245E4B871B871023F96832DCA3A4BA3E8628C34ACB48C75497CB8949CA48D1EF939495F2A0BE4B7497E0C19659EBE083ABFD8268D97149418C969CE28112F31255383994AA95B50C7A15285477A6D01B955E80C9F961FD03226C8233CA6F4851318D0B22B5B0E4D536CDF729827F2A12289E789675DDE3BBDC339376447AF09CD807AF811D216D148126B42177D7F1634BFAB0BB959A485BE82F7CE08FA8468FE526D48B02CA70CAF5EA55B786E7659DAFEFFC8292E15C251BC48D27F15860BD32E2FB67FB70DDED2CB7D199ECF107FEB5F57CA6D7D83ACA47DD20D23E3F7F73AF93753F1D6E6C42060A2F0A19CA9905CFCA4705F8DA96287D57584E9D0C9FEE127A1F8E91E6AA112FDD0AA42714BBFBDF1DB07BED4D3BB70B2AE3D614F75E17B8932E3ADCB8077DBE6EB9A3B723DFE7000B0B8DAD199D8FF4B8501BE45671BCAA8F3F5A9EB9EE67805F91C0734BE00F7EFDEAD031308879A852612AE3910830086EF4BC3CD6F9C14C5FA50F563EAB57C89F6AA49BBDF923D5E8847017C2F134AC4777E4E52D1DDDC1CCDDF800CC07DE1E733C8D233508E88306A0C9A035B1B61FA386F10CB1841C05C3442CAC764B0A5276A1047BF6EFA0E621A2FAE1A8792D8C5E20F692A472D88F96B32EB3D18B066BBEC04DAC120ADD3A0AFDAA2D81DF0A2CAFD1C135A0EC7AAEF4474B2853C125487DE8A7623F25F0029F912F9F689DD0AD5F4275FC8DFB6ADD908B677D3975AFBC207B0B24D225EDF28F88C17C451D6F0A8521CA55B873F611C742C5C7525B04C6C3E2BA0BC59D43C02EE517BA8D08E102F9837A6B37C505D2BD97D23AB4F6912B5EB67747EB572969057B923D347980E7F3338F2E70AE1E13B2071D9DD84991937B676838F8C42BB6A36A06A78B895063CBF9E20FD445EC96CF886D58FCA47230593FE7DA25535BBDAD2BED116FCF0A47BFEE90F6C0C227A5B9DFA33BDAB645585EBD3CC402DE595FF1A016A1B73472580FB2CB271CCEDFF473916D72334E4D5F4674EBA649636B00D05C852FFDF930360DCEFF949BEA357AF1DE79DD503E9705BAE51488F3B5F4468F15FC17593B7C06E2E5D7A26D02112E28034ED3D5C2956159CD2440D8B03BBA8E227608FE9C12FF0C0A12600AE3A3938AF7DDAB4BED9243A891D4EE684F5A0EC60DA908C5167F0302BBFB8940817D4C7D2F242DB6A980F196A2FF973223D73866B4E226D3F6EEB8177536FB10DA9E7BD864B0020C636F3A3673761A17B6865992FB0755AE9EB8036AA41776294D0FF8EA6F12CC9ECB45D45B154F2BF03B0A70E2B42DA1A7F99AA3FD4819857118FD77666D476C3C9BD258377994FB49EB5E820B416CCC5449895DEF2EAE3637CC8D5828D9DA7F1727FAEB740A7148BE35A4A689C75D152DD4DD431EAEA135E3AC5384BF7A226971B5BE18E041D046843F9BE8552292DF886C97F010DE239C4DD431163A88AB440BF14BD8B69D409C48366F289E59282EDE9796CAD4A1975FF52A2332DAC6756CB25AA24273B90E22B2B133A5C3F0805160E510B192D6BC18370F43181AC300D06092B06010401823711023100301306092A864886F70D0109153106040401000000302706092A864886F70D010914311A1E1800540053005300650063004B006500790053006500740031305D06092B060104018237110131501E4E004D006900630072006F0073006F006600740020005300740072006F006E0067002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072
1497:d=1 hl=4 l= 879 cons: SEQUENCE
1501:d=2 hl=2 l= 9 prim: OBJECT :pkcs7-encryptedData
1512:d=2 hl=4 l= 864 cons: cont [ 0 ]
1516:d=3 hl=4 l= 860 cons: SEQUENCE
1520:d=4 hl=2 l= 1 prim: INTEGER :00
1523:d=4 hl=4 l= 853 cons: SEQUENCE
1527:d=5 hl=2 l= 9 prim: OBJECT :pkcs7-data
1538:d=5 hl=2 l= 28 cons: SEQUENCE
1540:d=6 hl=2 l= 10 prim: OBJECT :pbeWithSHA1And40BitRC2-CBC
1552:d=6 hl=2 l= 14 cons: SEQUENCE
1554:d=7 hl=2 l= 8 prim: OCTET STRING [HEX DUMP]:135DB999CA2CD6B1
1564:d=7 hl=2 l= 2 prim: INTEGER :07D0
1568:d=5 hl=4 l= 808 prim: cont [ 0 ]
Again, let’s decode the nested structure.
$ openssl asn1parse -inform DER -in extracted_data.bin -strparse 26 -strparse 23
0:d=0 hl=4 l=1466 cons: SEQUENCE
4:d=1 hl=4 l=1462 cons: SEQUENCE
8:d=2 hl=2 l= 11 prim: OBJECT :pkcs8ShroudedKeyBag
21:d=2 hl=4 l=1270 cons: cont [ 0 ]
25:d=3 hl=4 l=1266 cons: SEQUENCE
29:d=4 hl=2 l= 28 cons: SEQUENCE
31:d=5 hl=2 l= 10 prim: OBJECT :pbeWithSHA1And3-KeyTripleDES-CBC
43:d=5 hl=2 l= 14 cons: SEQUENCE
45:d=6 hl=2 l= 8 prim: OCTET STRING [HEX DUMP]:66AFD4385D4302C4
55:d=6 hl=2 l= 2 prim: INTEGER :07D0
59:d=4 hl=4 l=1232 prim: OCTET STRING [HEX DUMP]:93F23B4782B6438E5CB094A8C35CF1352F486FA1F7E3708A3F1BFC865A5EEF3C931DC82BA36EEF23609FE4717D0A021EEF8A981021BDADD04AFA64131A546CE65191A88C001ADCA9A5A15EDB1178E0DADDDCEDDCC3AB13BAADAE35B2B87378CC9158C0145DB1EB300E129D265C92E2C726E4790DA9F34AD0B80AF7BFD152B7AF4DD97B9B3BC4057CA245E4B871B871023F96832DCA3A4BA3E8628C34ACB48C75497CB8949CA48D1EF939495F2A0BE4B7497E0C19659EBE083ABFD8268D97149418C969CE28112F31255383994AA95B50C7A15285477A6D01B955E80C9F961FD03226C8233CA6F4851318D0B22B5B0E4D536CDF729827F2A12289E789675DDE3BBDC339376447AF09CD807AF811D216D148126B42177D7F1634BFAB0BB959A485BE82F7CE08FA8468FE526D48B02CA70CAF5EA55B786E7659DAFEFFC8292E15C251BC48D27F15860BD32E2FB67FB70DDED2CB7D199ECF107FEB5F57CA6D7D83ACA47DD20D23E3F7F73AF93753F1D6E6C42060A2F0A19CA9905CFCA4705F8DA96287D57584E9D0C9FEE127A1F8E91E6AA112FDD0AA42714BBFBDF1DB07BED4D3BB70B2AE3D614F75E17B8932E3ADCB8077DBE6EB9A3B723DFE7000B0B8DAD199D8FF4B8501BE45671BCAA8F3F5A9EB9EE67805F91C0734BE00F7EFDEAD031308879A852612AE3910830086EF4BC3CD6F9C14C5FA50F563EAB57C89F6AA49BBDF923D5E8847017C2F134AC4777E4E52D1DDDC1CCDDF800CC07DE1E733C8D233508E88306A0C9A035B1B61FA386F10CB1841C05C3442CAC764B0A5276A1047BF6EFA0E621A2FAE1A8792D8C5E20F692A472D88F96B32EB3D18B066BBEC04DAC120ADD3A0AFDAA2D81DF0A2CAFD1C135A0EC7AAEF4474B2853C125487DE8A7623F25F0029F912F9F689DD0AD5F4275FC8DFB6ADD908B677D3975AFBC207B0B24D225EDF28F88C17C451D6F0A8521CA55B873F611C742C5C7525B04C6C3E2BA0BC59D43C02EE517BA8D08E102F9837A6B37C505D2BD97D23AB4F6912B5EB67747EB572969057B923D347980E7F3338F2E70AE1E13B2071D9DD84991937B676838F8C42BB6A36A06A78B895063CBF9E20FD445EC96CF886D58FCA47230593FE7DA25535BBDAD2BED116FCF0A47BFEE90F6C0C227A5B9DFA33BDAB645585EBD3CC402DE595FF1A016A1B73472580FB2CB271CCEDFF473916D72334E4D5F4674EBA649636B00D05C852FFDF930360DCEFF949BEA357AF1DE79DD503E9705BAE51488F3B5F4468F15FC17593B7C06E2E5D7A26D02112E28034ED3D5C2956159CD2440D8B03BBA8E227608FE9C12FF0C0A12600AE3A3938AF7DDAB4BED9243A891D4EE684F5A0EC60DA908C5167F0302BBFB8940817D4C7D2F242DB6A980F196A2FF973223D73866B4E226D3F6EEB8177536FB10DA9E7BD864B0020C636F3A3673761A17B6865992FB0755AE9EB8036AA41776294D0FF8EA6F12CC9ECB45D45B154F2BF03B0A70E2B42DA1A7F99AA3FD4819857118FD77666D476C3C9BD258377994FB49EB5E820B416CCC5449895DEF2EAE3637CC8D5828D9DA7F1727FAEB740A7148BE35A4A689C75D152DD4DD431EAEA135E3AC5384BF7A226971B5BE18E041D046843F9BE8552292DF886C97F010DE239C4DD431163A88AB440BF14BD8B69D409C48366F289E59282EDE9796CAD4A1975FF52A2332DAC6756CB25AA24273B90E22B2B133A5C3F0805160E510B192D6BC18370F4
1295:d=2 hl=3 l= 172 cons: SET
1298:d=3 hl=2 l= 13 cons: SEQUENCE
1300:d=4 hl=2 l= 9 prim: OBJECT :Microsoft Local Key set
1311:d=4 hl=2 l= 0 cons: SET
1313:d=3 hl=2 l= 19 cons: SEQUENCE
1315:d=4 hl=2 l= 9 prim: OBJECT :localKeyID
1326:d=4 hl=2 l= 6 cons: SET
1328:d=5 hl=2 l= 4 prim: OCTET STRING [HEX DUMP]:01000000
1334:d=3 hl=2 l= 39 cons: SEQUENCE
1336:d=4 hl=2 l= 9 prim: OBJECT :friendlyName
1347:d=4 hl=2 l= 26 cons: SET
1349:d=5 hl=2 l= 24 prim: BMPSTRING
1375:d=3 hl=2 l= 93 cons: SEQUENCE
1377:d=4 hl=2 l= 9 prim: OBJECT :Microsoft CSP Name
1388:d=4 hl=2 l= 80 cons: SET
1390:d=5 hl=2 l= 78 prim: BMPSTRING
This actually looks like a PKCS12 file, an archive format bundling certificates and a private key. We can extract a private key from this:
$ openssl pkcs12 -in extracted_data.bin -nocerts -nodes -out private.key
Enter Import Password: mimikatz
MAC verified OK
I guessed the password ‘mimikatz’ for the certificate file but we could have information on that here. After getting the private key, we can use a tool called RDP-Replay to replay the RDP session and figure out what the attacker was doing during the compromise.
After compiling, we can run the rdp_replay executable with options to save the
keys pressed by the attacker and to dump data from the captured clipboard
events to a file. Also, we save the replayed video to a file.
$ rdp_replay -r ../e8e2ceb9-b77f-4b26-b09a-fcec86e27497.pcap -o recording.avi -p ./private.key --save_clipboard --show_keys > output
Here is the recording of what the attacker did over RDP:
What he does is compress and encrypt the flag file with a password that is not displayed to the user, and then base64 encoded and copied to the clipboard. This is why we had to save the typed keys and clipboard event information.
The typed keys log:
RDP SSL MODE Requested by server!!
SSL private key found.
1024x756x8
REALLY DELICIOUS PANCAKES<Tab>REALLY DELICIOUS PANCAKES
The contents of the clipboard:
N3q8ryccAATjAlOVMAAAAAAAAABqAAAAAAAAACmoQ4fA1DQXZvCzJGIg/8cxnh8QXnWoDkwNxjGL
37P7rvVC2SMn8+wquEv/A5HBL9djQewBBAYAAQkwAAcLAQACJAbxBwEKUweBdxD1DDirkCEhAQAB
AAwrJwAICgGwcALcAAAFARkJAAAAAAAAAAAAERMAZgBsAGEAZwAuAHQAeAB0AAAAGQAUCgEAAFNu
lssb0wEVBgEAIAAAAAAA
Putting it all together:
$ cat ../clip-00000000-down | base64 -d -i > flag.7z
$ 7z x flag.7z
7-Zip [64] 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18
p7zip Version 9.20 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,2 CPUs)
Processing archive: flag.7z
Enter password (will not be echoed) :
Extracting flag.txt
Everything is Ok
Size: 39
Compressed: 186
$ cat flag.txt
HITB{44519a67ffc654e40febc09e20e8e745}
Flag: HITB{44519a67ffc654e40febc09e20e8e745}

Leave a Comment